Read Binary Bits with these effective methods
Created: Fri 28 Jul 2023 Updated: 7 months, 4 weeks ago

You are most likely familiar with the concept of Binary Language. Yes, you guessed it right. It's the language that modern Computers understand. Binary consists of 0 and 1. For the human mind to make sense of Binary Language is very hard because it's not meant for us. Below is a typical example of how a binary code looks like:
01001000 01000101 01001100 01001100 01001111
This binary bit just represents "Hello" in ASCII Characters (In English). If you are curious like me about how we can manually convert the binary bits into understanding English characters, then you are where you should be. Let's explore together how we can crack binary bits manually.
There are a couple of ways to convert binary bits back into ASCII Characters but we will be exploring two most convenient ways.
Method 1: Crack Binary using 8-bit binary table
This method is essential to understand the basics of binary to ASCII conversion. ASCII (American Standard Code for Information Interchange) is a character encoding standard that assigns a numerical value from 0-127 to represent characters and symbols.
In ASCII, each character consists of 8-bits (0-7). Each bit in the sequence of 8-bits can be either 0 or 1. To understand better, below is an example of representing 'H' character (in capital):
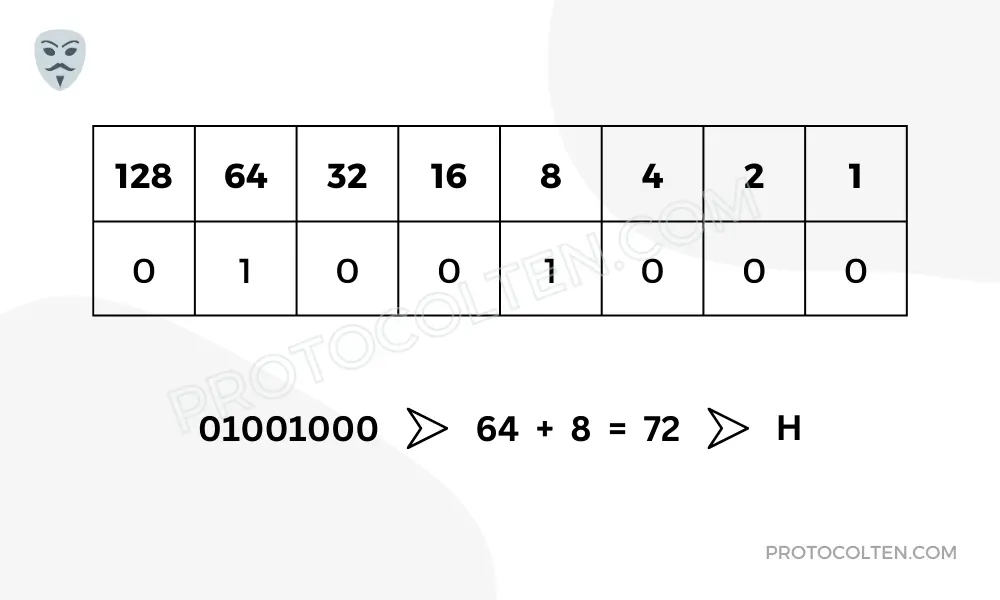
In the above image, we have been given a binary bit of 01001000. This bit converts to a decimal number of 72 which in ASCII represents 'H'. The conversion of binary bits to numerical is very straightforward.
- First, create a sequence of decimal values of the power of 2 in descending order. Which is 128 64 32 16 8 4 2 1
- Now assign each binary bit to a value in this sequence.
- Write down the decimal value that corresponds with binary 1 and neglect the value that corresponds with binary 0.
- The sum of decimal values that correspond with binary 1 will be our decimal number.
- Find that number in ASCII Character Table and that will be your character.
By implementing the above method, let's say we want to crack 01110000 01110010 01101111 01110100 01101111 01100011 01101111 01101100 01110100 01100101 01101110 into human-readable ASCII characters. This is how we do it:
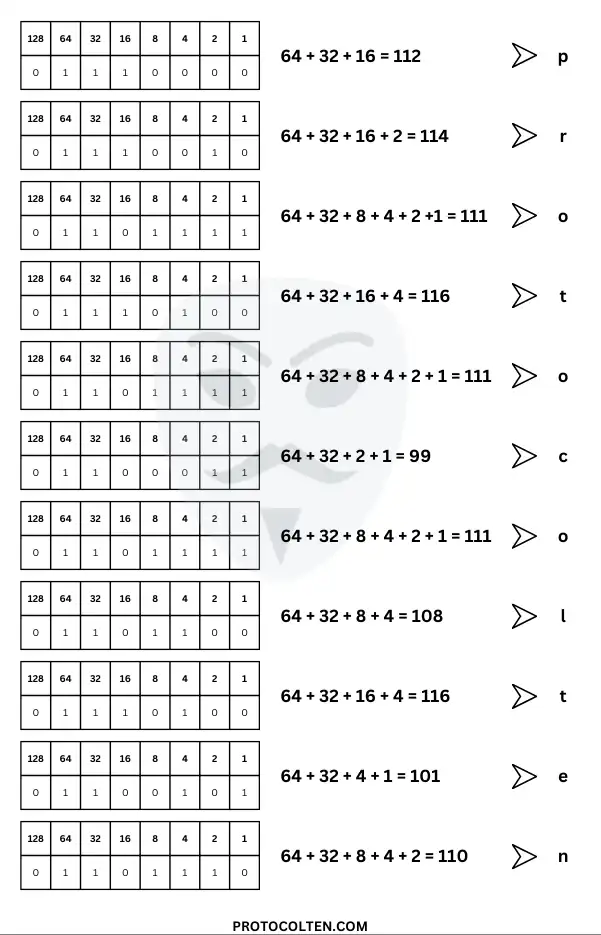
By using the 8-bit binary table method, we cracked the given binary bits that say protocolten in ASCII characters.
Method 2: Convert and read Binary bits
This method is a little bit different from the first method. But if you understand the first method clearly, then the implementation of this method will be easy. Just like the first method, we have binary bits 01001000 that we need to convert into ASCII character. Look at the image below to get an overview of how this method works.
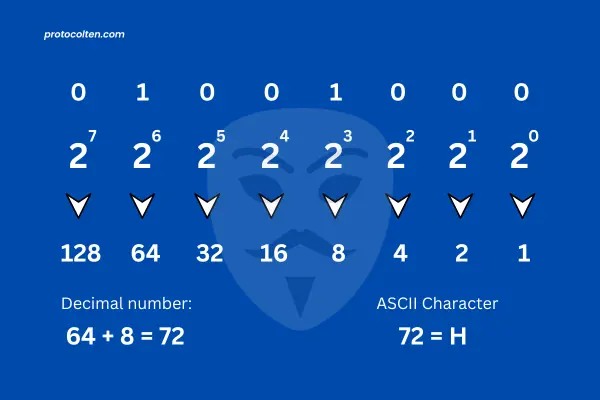
Unlike the first method, we don't need to create a binary table. We have been given binary bits. This method works by utilizing the power of 2. In 8-bit binary code like 01001000, classify each bit with 2 and power of 2 will be the bit position in that 8-bit sequence.
So the leftmost bit will be the most significant and the rightmost bit will be the least significant. In this order, the leftmost bit will have 27 (bits start from 0-7 backward) and the rightmost bit will have 20. By using this method we can simply assign a value to each bit and then this value will be converted into a decimal number. We need only the bits with 1 and neglect the bits with 0.
This way when we assign 2(0-7) values to 01001000, we will only keep 26 and 23 because there are only two bits of 1 and those bits corresponds with 26 and 23 respectively. These bits represents 64 and 8 (26 = 64 and 23 = 8) in decimal number. The sum of these bits is 72 and this decimal number represents the 'H' character in ASCII Character table.